Consumers are under siege by cybercriminals posing as well-known and trusted brands. According to Verizon, almost 36% of all data breaches involve phishing, with 55% of phishing websites masquerading as trusted brands. While many assume phishing attacks are solely related to email, this is untrue. Attackers frequently use social media, malicious ads, and fake domains in an attempt to phish information out of consumers.
As a corporate entity, it is crucial to understand the nature of how cybercriminals utilize these attacks in order to prevent exploitation of your brand. This article examines the most common forms of brand attacks criminals use to target your data and presents practical tactics to avoid becoming their next mark.
How Brand Attacks Steal Info
Brand attacks are a unique variety of cyber-attack involving trusted brands that criminals use to trick consumers into revealing sensitive information. Cybercriminals masquerade under the identity of well-known and trusted brands to reduce the likelihood of users catching on that they are being deceived. They use attacks such as fake websites, phishing, or social engineering tactics to convince users to willingly turn over their personal data as the user believes the request originated from a trusted source.
Attack Methods
There are several methods attackers use to launch brand attacks, each with its own unique characteristics. The most common brand attack methods involve the following:
- Phishing kits – Tools and resources allowing attackers to create fake login pages or other online forms to trick victims into giving up their personal information. These pages are often identical to the legitimate brand’s login pages, making them difficult to distinguish from the real ones.
- Cloning websites – Involves creating an exact copy of a legitimate website, down to the most minor details, and hosting it on a different domain. The attackers then use various tactics to lure unsuspecting users to this cloned site, where they can steal sensitive information or deploy malware.
- Malicious Ads – Attackers create ads impersonating legitimate brands tricking users into clicking on them and leading them to phishing pages, malware downloads, or other attacks. These attacks may be augmented with social engineering tactics to convince users that the ad is legitimate, increasing the chances of a successful attack.
The target
End-users are a prime target for brand attacks, placing their personal data at risk. This data could include payment information, login credentials, and private information stored on other sites. The ultimate goal of these attacks is to steal the user’s information, including login credentials and payment information, which can be used for fraud or identity theft. With malicious domain names often being similar to legitimate ones, it is easy to overlook the red flag and continue to the site, especially if it is a clone site.
Clone sites use branding identical to the legitimate site, further convincing users that they are on a safe and trusted website. Such as in an attack identified by Bfore.Ai targeting one of the biggest banks in Ireland, Bank of Ireland, where threat actors created a cloned login site for the bank. Users accessing what appears to be a legitimate website may inadvertently give their login credentials, which attackers use to access the actual site in their place. This results in the theft of stored payment information and attackers making purchases on the account while sending merchandise to themselves. Attackers will then store these credentials for future password-stuffing attacks, where the same credentials are used on multiple sites to gain access to other accounts.
Users may even attempt to purchase items through these clone sites, and inadvertently provide their credit card numbers, which cybercriminals collect and use for future purchases or sell on the dark web. Such as in the attack on Media Markt where products were being sold at a lower price point on a brand impersonated website. Attackers may even send actual merchandise to buyers to make the scam appear more legitimate.
Malicious Domain Red Flags
Cybercriminals utilize malicious domains to lay the foundation for larger attacks against businesses and individuals. Understanding what to look for will help protect you from these attacks.
Malicious domains are often registered with misspellings and variations on well-known brand names to trick users into thinking they are accessing legitimate sites. These misspellings can be subtle, such as omitted or duplicate letters, which can be difficult to detect visually. In addition to misspellings, malicious domains may use URL obfuscation techniques to conceal the true destination of a link. For instance, they may use a long string of characters or random words in the URL to make it difficult for users to decipher.
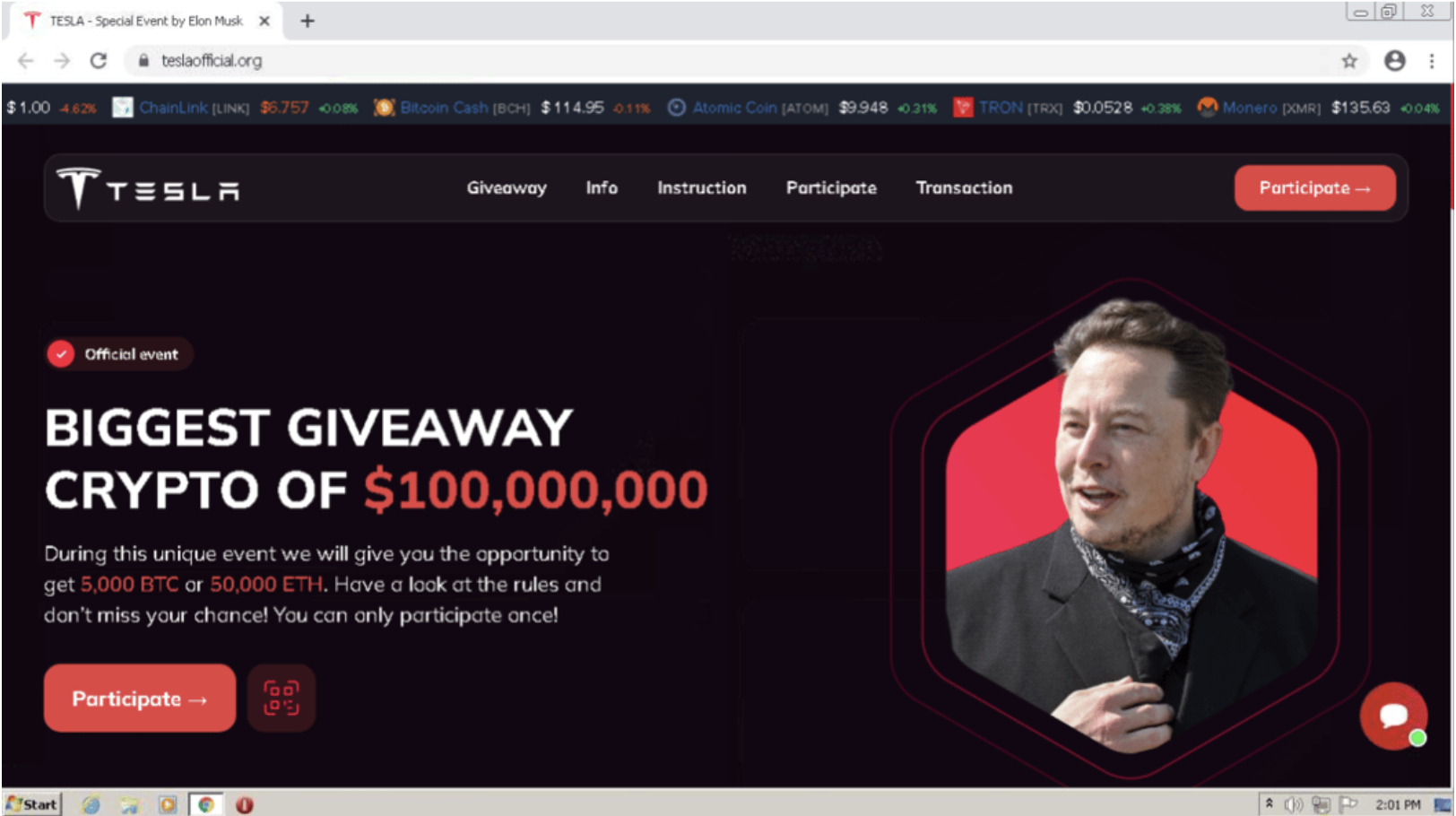
These attacks are further complicated by suspicious top-level domains (TLDs), such as .biz, .info, or .pw, which are less common and often associated with malicious activity. By changing the top-level portion of the domain, the rest of the name identically matches the original, making it harder for users to identify such as teslaofficial[.]org to impersonate tesla[.]com. Phishing attacks take this a step further by swapping out IP addresses for domain names in the URL, so the text shows a standard URL, but the link underneath is altered.
Malicious domain path
Malicious domain attacks follow a standard pattern used repeatedly, regardless of the targeted brand.
- Reconnaissance – Find a target brand and gather information.
- Purchase domain name – Purchase the domain to be used.
- Setup DNS records – Create DNS records that map the new hostname to an IP address.
- Build a website – Either copy the site directly or use a phishing kit to automate the development of a phishing site.
- Setup server – Create a server to run the website and collect information. This system may even install exploit kits to directly attack visitors and push malicious content onto their systems.
- Lure victims to the site – Use phishing, smishing, ads, social media, and shortened URLs to trick users into visiting the site.
- Steal information from victims – As victims visit the site, collect all possible information such as names, usernames, passwords, and bank details.
- Collect Profits – Sell information on dark web marketplaces or Telegram for immediate profits or use the data to steal victims’ identities and money.
Good vs. Bad
Identifying good and bad domains and websites is essential to avoid becoming a victim. There are several key indicators to look out for that can help you differentiate between them. The first is legitimacy. Good domains are typically publicly registered by the legitimate organization in order to ensure validation and ownership over their domains. Bad domains on the other hand, will not have any organization validation in their records and often limit the visibility over domain ownership.
Content is also crucial, with good domains typically having high-quality, original content relevant to their business or organization. In contrast, bad domains often have poor quality or plagiarized content. When deciding on the safety of a site, the user experience is a strong indicator. Good domains invest in UI/UX designers and often offer positive user experiences with easy-to-navigate web design, fast page load times, and clear calls to action. Alternatively, bad domains do not have the same level of time investment and may suffer from poor design, slow page load times, or broken links, making them frustrating and time-consuming to use.
Another key indicator is brand similarity. Good domains have a unique and distinct domain name that is easily recognizable as the brand’s official website. In contrast, bad domains often use brand name variations, punycode, misspellings, or other similarities to trick customers. Punycode is an internet standard which allows web browsers to generate domain names that contain non-Latin alphabets. For example, the city München would be encoded as xn--mnchen-3ya. Bfore.Ai identified a malicious login page for Banco Ciudad which used this method to mimic the legitimate domain as closely as possible. The threat actors used the domain xn--hb-bancciudad-2kb[.]com, which displays in the browser URL bar as hb-bancòciudad[.]com, and is very similar to the legitimate login domain URL, hb[.]bancociudad[.]com[.].
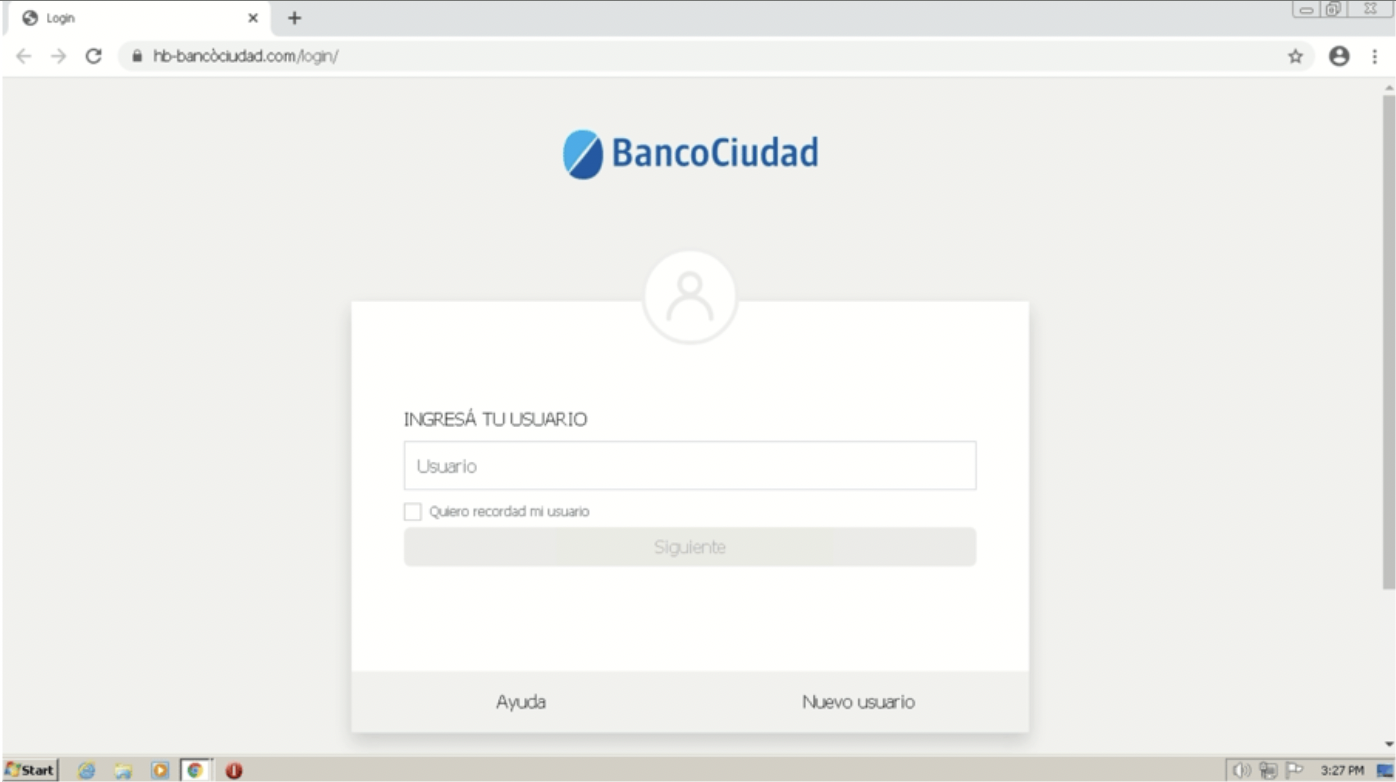
Fake login page for Banco Ciudad using punycode
Ways to protect yourself
Considering how common brand attacks are, understanding how they work is crucial for defending yourself against possible attacks. Below are some tips to help you avoid becoming a target of cybercriminals:
- Don’t follow links from emails: Cybercriminals often use emails to trick unsuspecting users into clicking links that lead to phishing pages or malware downloads. Avoid following links from emails, especially from unknown or suspicious sources.
- Check the certificate before buying: Before spending money online, check to see if the website has a valid SSL certificate. Legitimate websites will have an SSL certificate, and the URL will start with https:// instead of http://, showing the site is secure and that any information you enter will be encrypted.
- Carefully read the website name: Cybercriminals create websites with names similar to legitimate brands or companies. Take the time to carefully read the website name before entering any personal information or making a purchase.
- Don’t follow links that use compressed formats such as bit.ly: Cybercriminals often use compressed links to hide the true destination of a link. Avoid following these links, which could lead to phishing pages or malware downloads.
- Check brand reputation using online reputation services: Online reputation services such as Google Safe Browsing, Norton Safe Web, or McAfee SiteAdvisor can help you determine if a website has a good reputation or is associated with suspicious activity. Check the reputation of any site before entering personal information or making a purchase.
Following these simple tips can help protect yourself from online threats and stay safe while browsing the web.
Stopping Brand Attacks
Companies are responsible for keeping their customers’ data secure and must therefore remain vigilant to any threats targeting their brand to protect their identity and reputation. Stopping these attacks as fast as possible helps mitigate the amount of damage caused, keeps your customers safe and prevents them from associating brand attacks with your organization. Doing this requires partnering with a trusted security provider like Bfore.Ai.
Bfore.Ai uses Prediction and PreEmption services powered by machine learning and artificial intelligence to quickly identify and preempt potential cyber threats. By leveraging cutting-edge technology, Bfore.Ai can help organizations stay ahead of emerging threats and minimize the risk of significant data breaches and financial losses using our PreCrime Technology.
 Don’t wait until it’s too late to protect your brand identity. Contact Bfore.ai today and let us help you stay one step ahead of the cybercriminals !
Don’t wait until it’s too late to protect your brand identity. Contact Bfore.ai today and let us help you stay one step ahead of the cybercriminals !