
“A lie can travel halfway around the world while the truth is still putting on its shoes”
The weaponization of malicious information, mainly through Foreign Information Manipulation and Interference (FIMI), is a growing concern for organizations. Recent cases such as the Medibank ransomware attack, the fake Eli Lilly Twitter account causing stock loss, and the Silicon Valley Bank (SVB) run initiated through WhatsApp demonstrate the potential impact of FIMI tactics on businesses and society. A recent PWC report showed that false news reports are 70% more likely to be retweeted than real news stories—organizations targeted by misleading information experience significant reputational damage, impacting their long-term revenue.
As these attacks become more sophisticated and widespread, it’s essential for organizations to take proactive steps to prevent themselves from falling victim to these attacks, monitoring and blocking unauthentic activity before it creates harm. This article explores the challenges of dealing with malicious foreign interference and examines how to prevent these attacks.

Source: ISPI
Foreign Weaponization
In the age of instant information, a company’s reputation is everything. A single negative news article or social media post can quickly spiral out of control and cause lasting damage to a business’s brand. While cyberattacks are typically associated with stealing sensitive information or financial theft, there is another type of attack that can be just as detrimental – Foreign Information Manipulation and Interference.
FIMI is a mostly non-illegal pattern of behavior conducted by state or non-state actors that aims to impact values, procedures, and political processes negatively. These activities are manipulative in nature, often undertaken intentionally, and executed in a coordinated manner. While disinformation is a prominent part of FIMI, the emphasis is on manipulative behavior instead of the truthfulness of the content delivered.
The end goal of FIMI is to cause reputational damage to the target, but there is often a larger agenda for the threat actors. An example would be political disinformation campaigns launched to sway an election or create unrest within a country. Sometimes, the goal may be to disrupt economic or diplomatic relationships.
The impact of FIMI on a business can be significant. Negative news articles or social media posts can quickly spread, causing reputational damage and losing customers, revenue, and even partnerships. This damage can be long-lasting and difficult to repair, even after the attack has been identified and addressed.
Dangers of FIMI
FIMI can pose significant dangers to organizations as it shifts the target from what they may expect, such as sensitive information like financial data or company secrets, to their brand. Many organizations may not have adequate defenses to protect their brand from such attacks. FIMI is often conducted intentionally and in a coordinated manner, so it can be challenging to detect and respond to effectively. The reputational damage caused by FIMI can have lasting effects on a business, leading to a loss of customers, revenue, and partnerships.
Different threat actors employing FIMI/Disinformation
Threat actors, particularly those from Russia, employ both traditional methods of attack such as malware attacks, and psychological methods of attack by, for example, spreading disinformation about a country’s politicians. Disinformation involves intentionally spreading false or misleading information. These campaigns are often launched around moments of political upheavals, such as a presidential election. Such campaigns can undermine the credibility of democratic institutions, sow division and distrust among the public, and ultimately, threaten national security.
By targeting public perceptions, threat actors can ensure dominance over the information landscape and attain information superiority over their adversaries. Information warfare is considered by some as more effective than traditional weapons, as it can degrade troop morale, discredit leadership, and undermine the military and economic potential of the enemy.
Social media amplification by swarms of fake accounts
In order to spread disinformation or FIMI, automated online accounts known as bots or groups of bots, botnets, are commonly used. These bots can be used for different purposes, such as spreading malware, or in terms of FIMI, using an algorithm to automatically produce social media content to emulate and alter human behavior at a large scale. In 2020, for example, a botnet codenamed “Fronton” (“Фронтон” in Russian), was identified with the capability to formulate, generate and deploy trending social media events to distribute inauthentic content. Examples include flooding Facebook with negative reviews about a company or restaurant, pushing conspiracy theories related to QAnon and Covid-19 on Twitter, or amplifying the number of likes on a post to promote it and generate the public perception that the message is more popular or widely supported than it actually is.
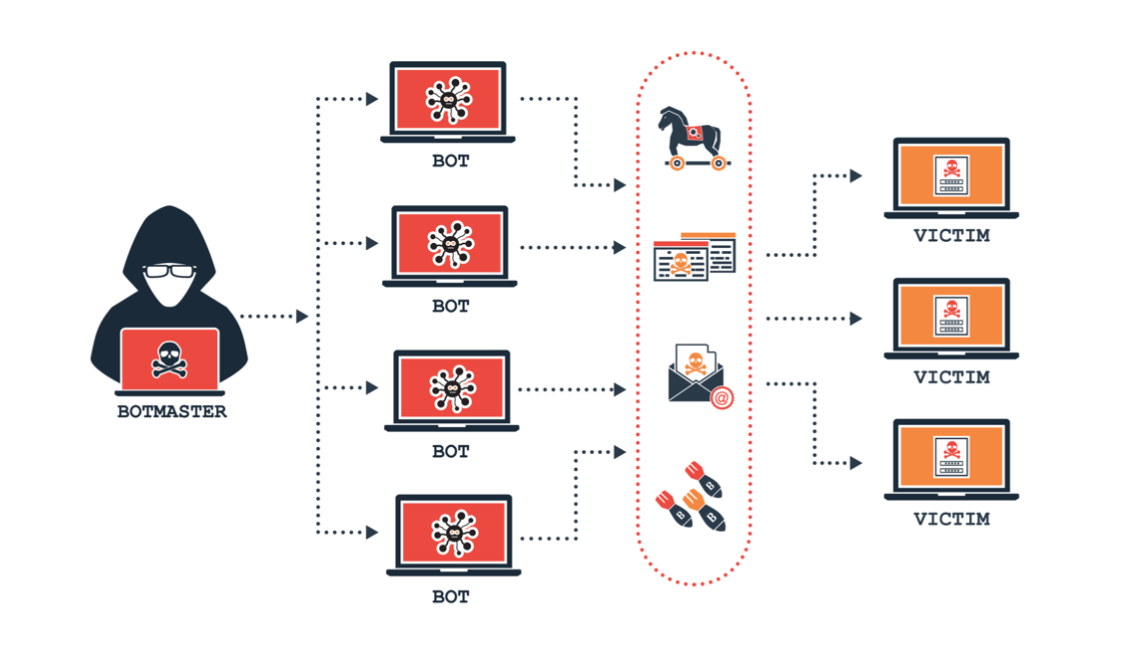
Source: Adam Levin
Recent Possible Cases of FIMI
Recent cases of FIMI attacks have raised concerns in the cybersecurity community. While the attackers behind these incidents have not explicitly stated their intentions, there are strong indications that they are engaged in FIMI operations. These attacks have targeted high-profile organizations and individuals intending to cause reputational damage rather than stealing data. This sets them apart from traditional cybercriminals typically motivated by financial gain. FIMI attacks can be severe, eroding customers’ and stakeholders’ trust and confidence in the affected organizations.
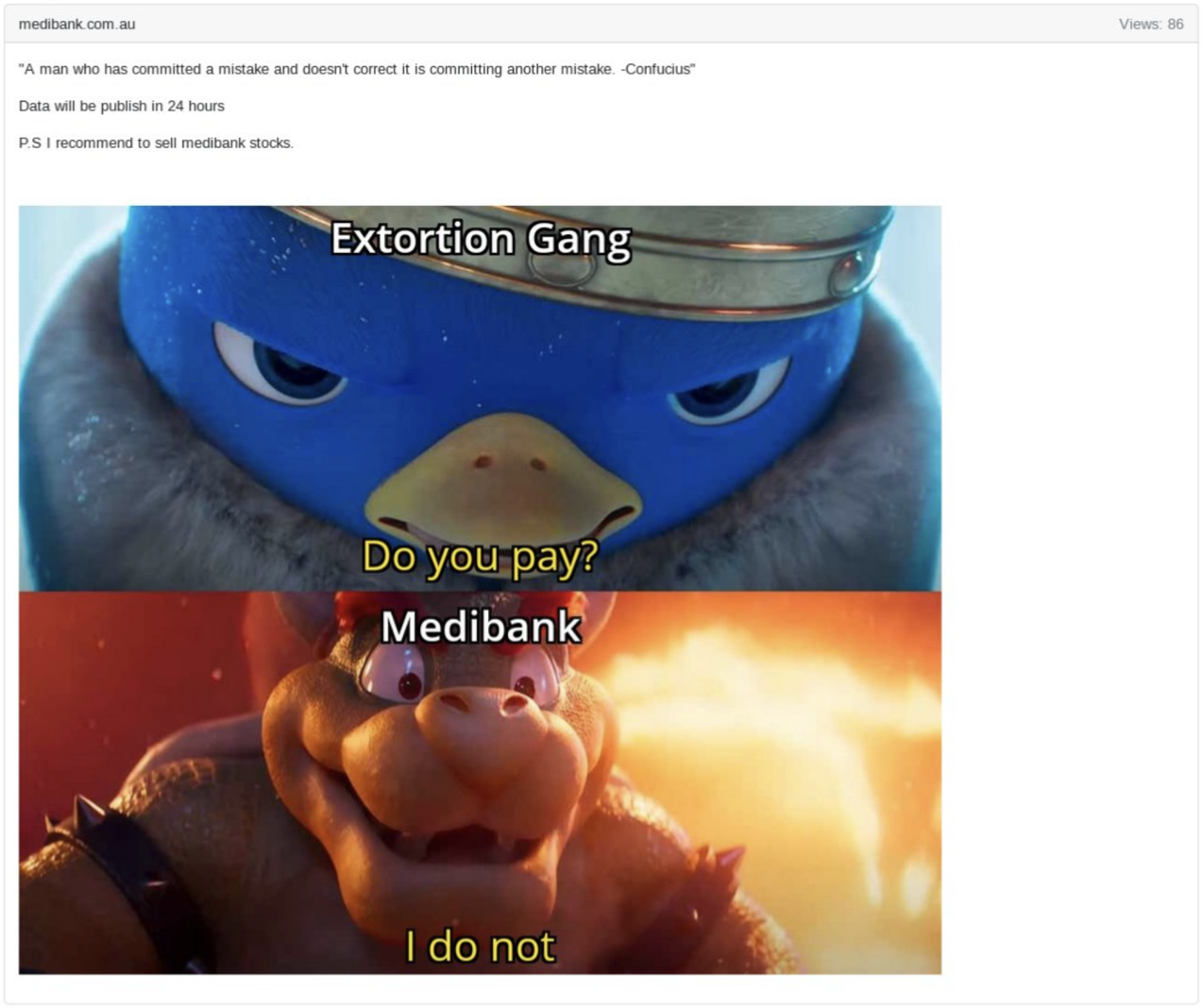
Medibank
In 2022, Medibank, a prominent Australian health insurance company, suffered a ransomware attack that resulted in the theft of highly sensitive data. The Russian group attributed to the attack, BlogXX, threatened to leak the stolen data from Medibank’s systems within 24 hours unless they were paid $10 million in ransom. Additionally, as shown in the screenshot below, BlogXX informed viewers to “sell medibank stocks”. This suggests we may be dealing with a FIMI operation rather than just a traditional ransomware attack as ransomware operations often cause significant reputational damage. In this case the goal is to manipulate public discourse via the stock market to erode confidence in Medibank.
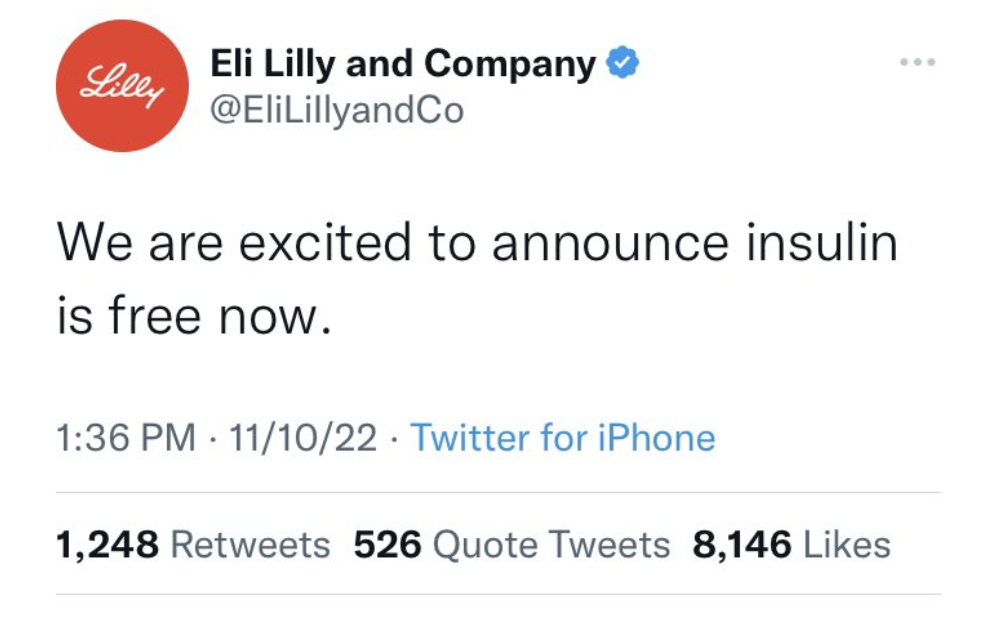
Eli Lilly
In a malicious attack in 2022, a fake Twitter account claiming to represent Eli Lilly, a major pharmaceutical company, announced free insulin for all, causing a significant stock loss for the company. The misinformation was amplified by unauthentic botnets, causing widespread panic and backlash against the company. This attack not only angered Eli Lilly, but it also caused them significant reputational damage and loss of stock value. Furthermore, this incident furthered conversations about the high price of insulin and access to life-saving medication. Twitter is believed to have also lost millions in ad revenue from Eli Lilly due to this attack.
Silicon Valley Bank
The SVB bank run started in a WhatsApp group where 200+ Venture Capitalists and Founders received notes from trusted account holders that “we are taking funds out.” This message initiated a panic run on the bank as the message spread, leading investors to lose faith in the bank and withdraw their money. Even larger banks are susceptible to this tactic, which can result in massive and rapid drains on existing funds. In the case of SVB, the panic caused by the WhatsApp messages led to a run on accounts, ultimately resulting in the bank’s collapse. In this situation it is not unreasonable to think that FIMI botnets may have assisted in the collapse by amplifying the initial message of withdrawing funds to spread fear in other customers and cause them to do the same. A 2018 study, for example, found that out of 9 million financial related tweets, 71% were classified as bots. Additionally, the World Economic Forum have reported that botnets are “increasingly being used to produce synthetic social media content positioned to induce withdrawals from fake “run on the bank” scenarios (impersonations of bank customers claiming to be unable to withdraw their deposits) and flash crash events (hacking and posting messages about fictional market-moving events on behalf of trusted accounts, like the Twitter account of a central bank chief)”.
Source: World Economic Forum
Protecting Against FIMI
As the number of FIMI attacks continues to rise, organizations must be proactive in adopting security measures beyond traditional security challenges. Protecting against FIMI requires a multifaceted approach that addresses technical vulnerabilities and reputational threats. Organizations must be open to defending their brand and reputation from attack through non-traditional routes, such as social media, fake news, and disinformation campaigns. This requires a shift in mindset from purely technical security measures to a more holistic approach that encompasses brand management and reputation protection.
Monitoring for Unauthentic Activity
Monitoring for unauthentic activity has become crucial to any effective cybersecurity strategy. Still, the modern attack surface is too vast for any organization to monitor and defend on its own. Despite best efforts to continuously monitor for unusual or suspicious activity across their networks and systems, organizations may have areas where their monitoring does not cover. This inhibits their ability to quickly detect and respond to potential threats before they can cause significant damage.
Effective monitoring is a continuous process that includes automated tools and human analysts who can identify and investigate potential security incidents. Organizations can improve their monitoring strategy by partnering with third-party security providers who can provide advanced monitoring and threat intelligence capabilities. These providers offer additional visibility outside the current implementation, eliminating blind spots.
Defending Reputation
Defending reputation is a critical part of any effective cybersecurity strategy. Proactively taking down fake accounts and sites is required to stop these threats effectively. However, this process cannot be undertaken without appropriate resources, as it is often challenging and time-consuming, requiring significant resources and expertise.
The process of eliminating fake domains and false accounts on different social media platforms is a complex process of evidence gathering, verification, and coordination with the relevant platform providers. Attackers frequently use multiple platforms and domains, making this all the more challenging and ensuring that even diligent organizations may miss an instance of fake accounts and sites. Even when bogus accounts and sites get removed, the threat is not over. Ongoing monitoring and follow-up are required to ensure they do not reappear.
A Partner In Protecting Your Reputation
To maintain trust with customers, companies have a responsibility to stay vigilant and proactively protect their brand identity. By stopping attacks early, organizations can keep their customers safe and prevent them from associating brand attacks with their company. Partnering with a trusted security provider like Bfore.ai can help companies achieve this goal. Bfore.ai uses advanced security solutions to safeguard your brand from the latest cyber threats and attacks. Our defenses continuously monitor your online presence for potential risks and provide real-time threat intelligence and incident response to prevent and mitigate attacks.
Don’t wait until it’s too late to protect your brand identity. Contact Bfore.ai today and let us help you stay one step ahead of the cybercriminals !





