Executive Summary
On July 19, 2024, a sudden outage affected a majority of primarily Microsoft devices following an update issued by CrowdStrike. Initial inability to identify the root cause of this sudden outage, resulted in a significant halt in global operations across a wide range of industries. According to a BBC report, approximately 8.5 million Windows hosts were frozen from day-to-day activities, and the severity of issues caused in medical, aviation, and other emergency
reasons was beyond imagination.
Following the recent update incident affecting Microsoft computers, malicious actors have registered various domains and typo squats targeting CrowdStrike, exploiting the situation for
malicious purposes. These domains are often crafted to resemble legitimate CrowdStrike addresses, intending to deceive users into divulging sensitive information or installing malware.
The motives behind the actions taken by these malicious actors range from financial gain through phishing and fraud to causing reputational damage to CrowdStrike by associating it with the fallout from the Microsoft incident. Additionally, some domains were registered to mock the situation, further amplifying the negative publicity and adding to the reputational risk.
Campaign Analysis
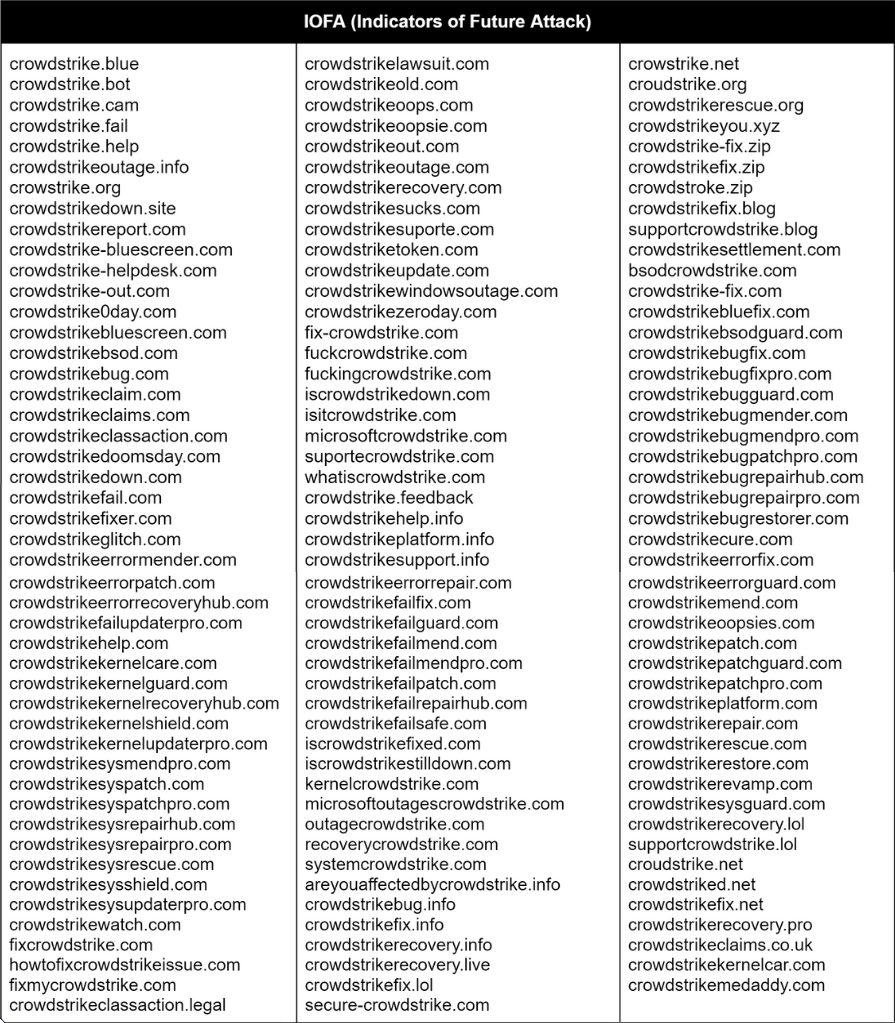
Within a week of the incident’s widespread impact, the researchers at BforeAI were able to identify 140 domains registered. The entire list of domains can be found here.
110 out of 140 domains were found to be either malicious or suspicious. 98 domains were confirmed to be malicious and the other 12 remained under observation for suspicious activity. The majority of the domains were also registered with a set of registrars, notoriously known for facilitating DNS abuse and phishing activities.
The trends show that domains registered for this purpose leveraged keywords such as, “kernel fix”, “helpdesk”, “CrowdStrike down”, “CrowdStrike recovery”, etc. These domains were aimed at luring customers seeking help with this issue, legal action, and class action lawsuits.They were flagged for phishing, malware, and spyware alerts by various other threat intelligence platforms.
Out of the 140, four domains were available for re-registration indicating that their malicious
campaign was concluded and was restricted during the peak of the outage.
Correlation and Patterns Identified
The majority of domains include “CrowdStrike,” suggesting a direct attempt to impersonate or associate with the official CrowdStrike brand. Words like “fail,” “down,” “sucks,” “oops,” “bug,” “error,” “glitch,” “classaction,” “lawsuit,” “recovery,” and “fix” are recurrent. These terms indicate a focus on exploiting perceived failures or issues, likely to undermine CrowdStrike’s reputation and incite fear or frustration among users.
Variations such as “crowstrike,” “croudstrike,” and “crowdstriked” indicate typosquatting tactics aimed at capturing traffic from users who misspell the domain name. In addition, terms like “bluescreen,” “BSOD” (Blue Screen of Death), “kernel,” and “0day” (zero-day vulnerabilities) suggest a narrative of severe technical failures and exploits.
Domains incorporating “helpdesk”, “support”, “fix”, “repair”, “rescue”, and “mend” indicate an attempt to pose as technical support or issue resolution services, likely for phishing or fraud. Domains such as “classaction” and “claims” imply attempts to spread misinformation or capitalize on potential legal fears.
Many domains are designed to mimic legitimate CrowdStrike services, aiming to deceive users into believing they are interacting with the official site. By highlighting terms associated with errors, failures, and legal issues, these domains aim to exploit user concerns and drive traffic through fear. The use of support and help-related terms suggests an intent to trick users into providing sensitive information under the guise of technical assistance. Some domains
appear to mock the situation (like “CrowdStrikeoops”, “CrowdStrikeoopsie”, and “CrowdStrikesucks”), potentially adding to the reputational damage.
Conclusion
This malicious activity not only threatens user security but also undermines trust in CrowdStrike’s brand, highlighting the need for robust domain monitoring and cybersecurity measures to mitigate such risks. Please find the identified malicious domains here.