
Cybercriminals have evolved far beyond the stereotypical “hacker in a hoodie” persona. By their very nature, they have to work together to improve their skills, offload ill-gotten gains, and discover more effective techniques. They turn to the dark web and other collaborative platforms to facilitate working together and upping their collective game. This is why dark web usage has spiked over 300% in the last 5 years, as droves of cybercriminals take advantage of learning from each other.
While it may be easy to assume this is a small problem, with only a few dozen bad actors out there, dark web forums alone contain over 8 million members, any of which may be actively conducting attacks. In this post, we will explore the dark underworld of how cybercriminals communicate with each other and collectively work to elevate their threat.
 Source ID Agent
Source ID Agent
Collaboration Tools for Cybercriminals
Threat actors work to stay ahead of the game to maximize their returns on attacks while avoiding being caught by authorities. They do this through collaboration and sharing of information and resources. This often involves anonymous ways of sharing to reduce the risk of being caught and provide a method of unloading stolen goods. Additionally, working with others allows threat actors to get their hands on the latest tools and learn about what is working and what is not.
How threat actors work with others depends on the type of threat actor. As discussed in a previous article, this can range from individuals working alone to organized groups. Understanding the kind of threat actors and their methods of operation is essential in combating cyber threats and ensuring the security of individuals and organizations.
Darkweb Forums
There are many online forums and marketplaces where cybercriminals can buy and sell goods and services, such as stolen data, malware, and hacking tools. However, access to many of these forums is often restricted, with some being invitation-only or requiring a referral from a trusted member to join. This helps to reduce the potential for law enforcement to infiltrate these forums and monitor their activities.
These restrictions often make it difficult for law enforcement to access these forums and track down cybercriminals. Using this approach does make it harder for law enforcement to gain access, but it does not guarantee they will stay out. Over time, many agencies have posed as attackers and worked their way into these forums, allowing them to monitor what occurs. This has also led to the founder and owner of one of the most popular Darkweb forums, Breached, to be arrested in March 2023, eventually leading to the forum being shut down by the forum’s admin.
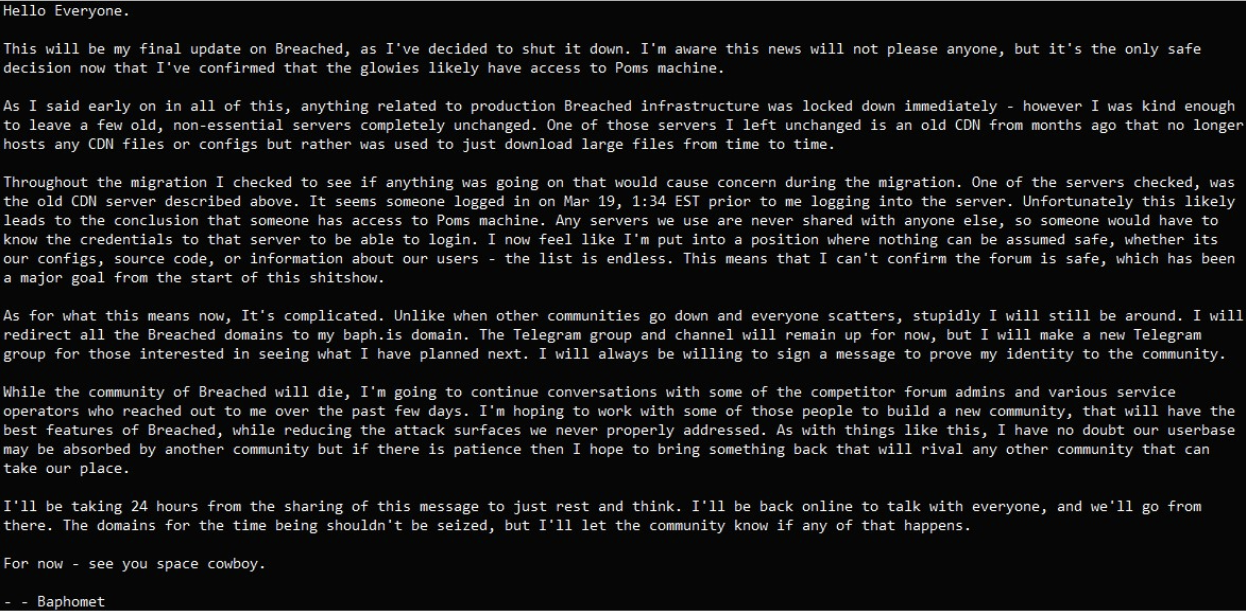 Breached admin, Baphomet shuts down the forum after the founder was arrested.
Breached admin, Baphomet shuts down the forum after the founder was arrested.
As more of these forums are being seized by law enforcement, cybercriminals have increasingly been migrating to the messaging app Telegram instead, including those left behind from the Breached forum.
Encrypted Messaging Apps
Cybercriminals often use encrypted messaging apps such as Telegram, Signal, and WhatsApp to communicate with one another while maintaining a high degree of secrecy and avoiding detection. They feel that the encryption in these messaging apps prevents snooping by authorities, allowing them to conduct business in private as long as they trust the parties they are communicating with.
The threat actor Fooble, for example, uses both a Russian Darknet forum and Telegram to sell credentials, as seen in the screenshot below. Fooble is a notorious Russian network access broker who offers compromised access credentials across several sectors, often derived from malware logs and automated marketplaces where stolen credentials are sold in bulk.
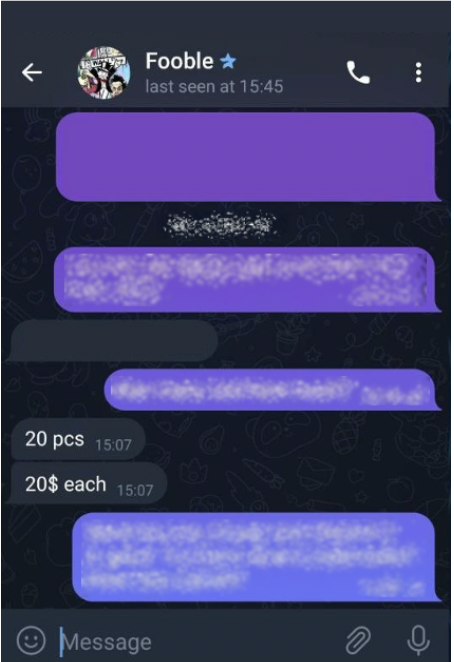
Threat actor Fooble selling harvested credentials in a private chat on Telegram.
While these messaging apps do prevent over-the-wire snooping, it is still possible for endpoints to be compromised or for man-in-the-middle attacks to occur. This means that even with encryption, cybercriminals are still vulnerable to having their communications intercepted or compromised. Even in situations where they are confident their transmission is secured, there is no guarantee that the individual on the other end of the conversation is not compromised or a member of law enforcement.
Chat Rooms
Chatroom communication is not a new concept despite its usefulness to cybercriminals. It has been utilized by various groups, including those in the gaming community, for years. Chat rooms are similar to messaging apps in that they allow for real-time information sharing. However, unlike messaging apps, chat rooms may have many participants chatting simultaneously, making them a valuable tool for cybercriminals who want to exchange information quickly and efficiently.
Cybercriminals often utilize chat rooms to communicate with each other, buy and sell goods and services, and share knowledge and expertise. This method of trading information has been around for decades, dating back to the early days of IRC services. Much like other forms of collaboration, these generally exist on private servers with limited access, making it more challenging for law enforcement to snoop on them.
 Darkweb private chat room.
Darkweb private chat room.
Darkweb Marketplaces
Cybercriminals often use the dark web to buy and sell goods and services, as these marketplaces are accessible only through the Tor network and offer a high degree of anonymity. This anonymity is essential for cybercriminals as they trust that the decentralized Tor network hides their use of these sites and keeps them anonymous.
While Tor does offer a level of anonymity, it is not perfect. Compromised exit nodes can monitor and intercept traffic, potentially exposing cybercriminals’ identities. In addition, while cryptocurrency transactions are often used to facilitate transactions on the dark web, they can be tracked in some cases, making it possible for law enforcement to trace transactions back to their source. This happened in 2021 when the world’s then-largest dark web marketplace was shut down by law enforcement after a coordinated investigation between multiple agencies. And now in 2023, another notorious marketplace known as Genesis, hosting around 80 million credentials stolen from more than 2 million people, has been seized by law enforcement agencies from several countries.
You can check whether your data has been compromised from Genesis marketplace via the Dutch police who were part of the investigation.
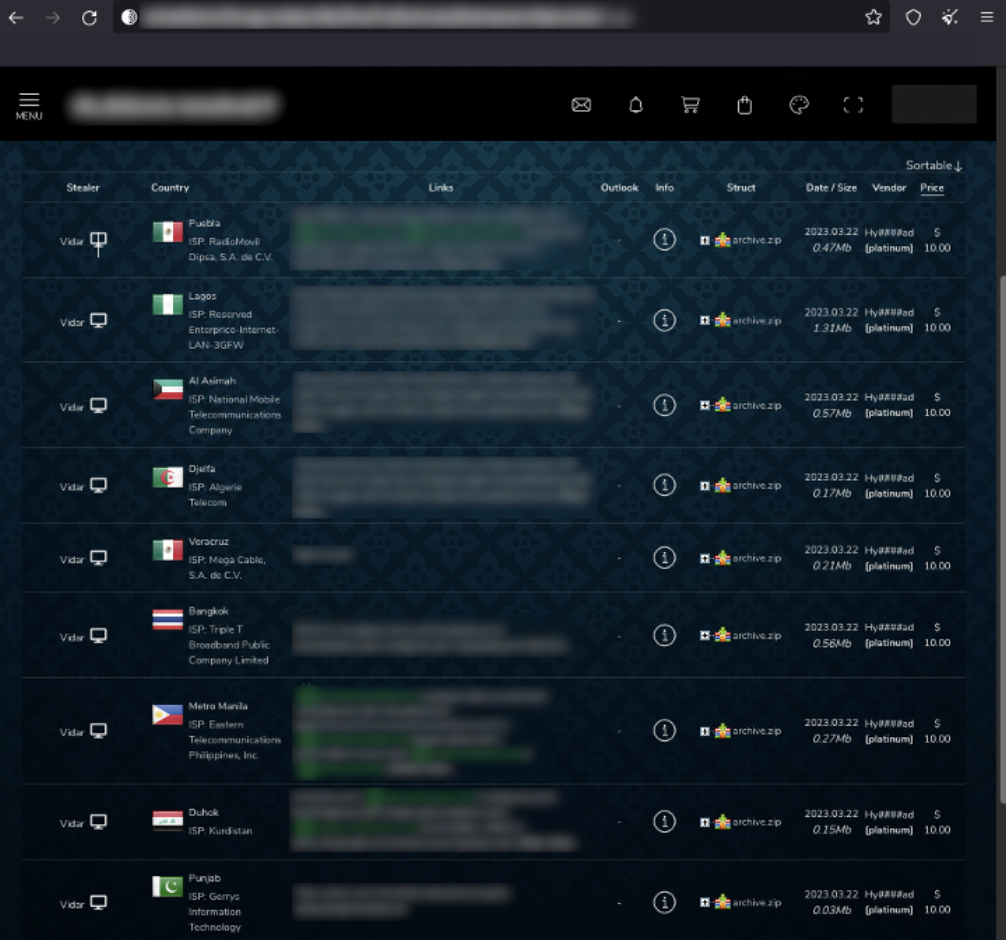
A Russian marketplace selling stolen account data from various websites.
Direct Contacts
One-to-one information trading is common among cybercriminals, allowing them to monetize stolen data quickly and efficiently using various contact methods such as email or phone. This method is typically reserved for when the cybercriminals already have a working business relationship or a direct referral by a trusted partner.
Even in these cases, criminals attempt to obfuscate their identities and limit the sharing of personal information to prevent being caught. This may involve using aliases, encrypted messaging apps, and other techniques to hide their true identities and locations.
Stay Ahead of Cybercriminals
As the landscape of cybercrime evolves, it’s critical to stay vigilant and take proactive measures to protect your brand identity. With new platforms and communication methods constantly being developed to evade detection, it’s more important than ever to partner with a trusted security provider like Bfore.Ai.
Our advanced PreCrime solutions are designed to safeguard your brand from the latest cyber threats and attacks. Whether monitoring your online presence for potential risks or providing real-time threat intelligence and incident response, Bfore.ai has the expertise and tools to keep your brand safe.
 Don’t wait until it’s too late to protect your brand identity. Contact Bfore.Ai today and let us help you stay one step ahead of the cybercriminals !
Don’t wait until it’s too late to protect your brand identity. Contact Bfore.Ai today and let us help you stay one step ahead of the cybercriminals !




